In Pakistan, the average smartphone user now spends more than four hours a day inside mobile apps, adding up to roughly 1,500 hours a year. That is nearly two full months annually spent operating inside platforms built not just to serve users, but to observe, record, and monetize them. Location trails, contact lists, messages, photos, browsing behavior, shopping habits, political interests, and health indicators are routinely collected as part of standard app usage.
What many users do not realize is how quietly this data is analyzed, shared, and in some cases exploited, often without meaningful consent or adequate safeguards. As enforcement struggles to keep pace, responsibility increasingly falls on users to identify risks early.
Permission Abuse Is the Loudest Warning Sign
One of the clearest indicators of invasive behavior is permission abuse. When an app requests access that has no logical connection to its stated purpose, it is rarely accidental. Flashlights and calculators asking for microphone access, weather apps requesting contacts, or note-taking tools demanding call logs and precise location are much more common than expected.
In 2026, any app requesting multiple high-risk permissions without a clear functional explanation should be treated as high risk, particularly when those permissions include camera, microphone, contacts, SMS, call logs, precise location, accessibility services, or overlay access.
Privacy Policies That Are Designed Not to Be Understood
Privacy policies often provide a second layer of insight. Apps that genuinely respect users make their policies easy to find and readable. Red flags include missing policies, excessively vague language, broad rights to share data with unnamed “partners,” or clauses allowing policy changes without notice.
If it is not immediately clear what data is collected, how long it is stored, and who receives it, users should assume the app prioritizes data extraction over user protection.
What Happens When You Say No to Permissions
How an app reacts when you deny permissions is often more telling than the permissions it requests in the first place. Well-designed apps are built to degrade gracefully. They explain why access is useful, allow users to continue with limited functionality, and respect the decision without disruption.
Suspicious apps behave very differently. Many will crash immediately, refuse to open, or trap users in endless permission loops that block all functionality until access is granted. Others display vague or misleading error messages such as “Something went wrong” or “Network unavailable,” even when connectivity is fine, creating the false impression that the app is broken rather than restricted by user choice.
Repeated permission prompts are another common tactic. Users may be asked for the same access multiple times within a single session, often after dismissing or denying it moments earlier. In some cases, the prompts are timed to appear after partial onboarding or data entry, increasing pressure to comply so that time and effort already invested are not lost.
More aggressive designs attempt to disguise permission requests entirely. Some apps present fake system alerts or use dark patterns that make denial options difficult to find. Others link critical functions to unrelated permissions, claiming that features like account verification, content loading, or security checks require microphone, camera, or location access, even when they do not.
These coercive behaviors are especially prevalent in low-quality loan, betting, and fake utility apps, where access to contacts, SMS, and storage is central to the business model. In documented cases, denying such permissions has prevented these apps from scraping contact lists or monitoring messages, which is precisely why they attempt to force compliance.
In contrast, legitimate apps typically provide transparency. They explain what will not work without access, offer alternatives where possible, and allow users to revisit permissions later. When an app cannot function at all without intrusive access, it is often because surveillance or data extraction is not a secondary feature, but the primary one.
Convenience That Comes at a Hidden Cost
Many apps disguise data collection as convenience. Requiring phone numbers, identity details, or full personal profiles just to browse content often serves data harvesting rather than functionality. Excessive OTP messages, unnecessary demographic questions, and forced sign-ups are all signals that user data is the real product.
Why the Developer Profile Matters More Than You Think

A developer’s profile is often the most overlooked yet most revealing part of an app’s listing. Patterns visible at the developer level frequently expose intent and behavior that a single app page cannot. When warning signs appear across multiple releases, they usually point to systemic practices rather than accidental design flaws.
One of the most common red flags is volume without variation. Developers publishing dozens or even hundreds of near-identical apps, often differing only in name, icon, or color scheme, are rarely focused on building quality products. This approach is commonly used to flood app stores with multiple entry points for the same data collection and monetization pipelines, increasing the chances that at least some versions evade enforcement or negative reviews.
Generic or disposable developer names are another indicator. Entities with vague titles, no clear company branding, or inconsistent naming across platforms often make accountability difficult. Legitimate developers usually maintain a consistent identity, public-facing website, support contact, and privacy documentation. When these elements are missing or deliberately minimal, it often signals an intention to disappear quickly if scrutiny arises.
Trackers, Background Activity, and Silent Monitoring
Even apps that appear harmless on the surface frequently operate as data collection engines beneath the interface. Independent privacy audits and mobile security analyses consistently show that basic utility apps, such as flashlights, photo editors, QR scanners, and wallpapers, often contain extensive networks of third-party trackers embedded deep within their code.
These trackers typically fall into three categories: analytics tools that monitor how users interact with the app, advertising frameworks that build behavioral profiles for targeted ads, and attribution services that track installs, referrals, and monetization pathways. While some level of analytics is standard, problems arise when a simple utility app includes dozens of trackers whose purpose has little to do with functionality and everything to do with profiling.
In practice, this means that a calculator or flashlight app may continuously transmit device identifiers, usage patterns, approximate location data, and interaction timestamps to multiple external servers. Users rarely see this activity directly, but its impact becomes visible through symptoms such as unexplained background data usage, rapid battery drain, or the app repeatedly relaunching itself despite being unused.

App Categories That Deserve Extra Skepticism
Certain app categories consistently present elevated privacy and security risks, and this pattern is especially pronounced in Pakistan’s mobile ecosystem. Loan, investment, betting, and so-called “earn money” apps have repeatedly surfaced in user complaints, regulatory warnings, and platform takedowns due to systemic abuse rather than isolated misconduct.
Digital loan apps are among the most problematic. Many request intrusive permissions such as contacts, call logs, SMS access, storage, and even accessibility services, far beyond what is required to assess creditworthiness. These permissions have been widely reported as being used to scrape contact lists, monitor user behavior, and exert pressure through harassment when repayments are delayed. In multiple prevented cases globally and regionally, such apps have leveraged personal data to shame borrowers by contacting friends, family members, or employers, turning privacy violations into coercive debt recovery tools.
Investment and trading apps present a different but equally serious risk. Fraudulent platforms often impersonate legitimate brokers, government schemes, or well-known financial brands, promising guaranteed returns or insider access. These apps frequently rely on aggressive onboarding flows that push users to deposit funds quickly while offering little transparency about licensing, custodial arrangements, or data handling. Many disappear entirely after short periods, only to reappear under new names with identical codebases, permissions, and backend infrastructure.
Betting and gambling apps, including unofficial sports betting platforms, are another high-risk category. These apps often operate in regulatory gray zones or outright illegally, using offshore servers and shell developers to evade scrutiny. They commonly embed extensive tracking frameworks, require permanent background access, and aggressively push notifications designed to drive compulsive behavior. Privacy policies, when present, are often copied templates that provide no meaningful disclosure.
The Battery Optimization Trap
Pressure to disable battery optimization is another common tactic. Malicious apps often seek permanent background access to continuously collect location data, audio, messages, screenshots, or clipboard contents. Legitimate apps rarely require this level of persistence. When a basic utility drains battery or data in the background, it is almost always intentional.
Fake Popularity and Manufactured Trust
Fake reviews remain one of the most effective deception tools. Sudden floods of generic five-star ratings, minimal criticism, and aggressive moderation of negative feedback often indicate paid install and review campaigns designed to manufacture credibility.

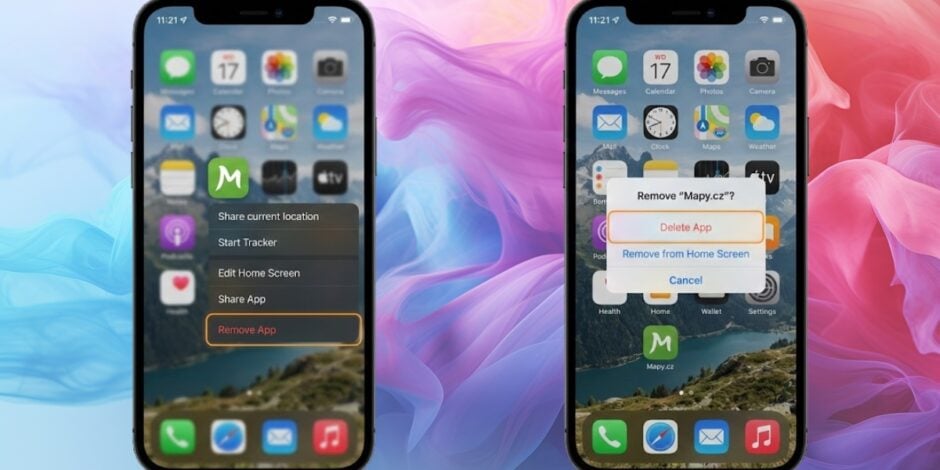
What to Do When a Spy App Crosses the Line
When multiple warning signs surface together, it is safest to assume the app poses a real risk rather than a theoretical one. At that point, hesitation often works in the app’s favor, not the user’s. The first step should be immediate uninstallation, followed by a review of all permissions previously granted to ensure nothing remains active in the background.
After removal, users should scan the device using a reputable mobile security or antivirus tool to detect any residual components, malicious services, or unauthorized configurations left behind. This is particularly important for apps that requested accessibility access, overlay permissions, or exemptions from battery optimization, as these can persist beyond normal uninstallation in some cases.
Passwords associated with accounts accessed while the app was installed should be changed promptly, starting with email, banking, and social media credentials. If the app involved payments, loans, or wallet access, users should closely monitor bank statements, transaction logs, and SMS alerts for unusual activity over the following weeks.
Reporting the app is equally important. Flagging it within the app store, submitting feedback to platform security teams, and sharing verified experiences in trusted consumer forums helps limit the app’s reach and alerts others. While enforcement can be slow, consistent reporting creates a documented trail that increases the likelihood of action.
Most importantly, users should resist the temptation to reinstall an app simply because it appears under a new name or promises fixes. Apps that cross privacy and security boundaries rarely change behavior. Walking away permanently is often the most effective form of protection.
Privacy Is No Longer Automatic

Privacy is no longer something users receive by default. It is a decision made repeatedly, often quietly, with every app installed and every permission granted. Platforms that genuinely respect users tend to follow clear patterns: they request only what is necessary, allow core functionality without mandatory accounts, explain permissions in plain language, and operate under transparent developer identities with traceable histories.
The reality is that most free apps are not free in any meaningful sense. They are subsidized through continuous data extraction, behavioral profiling, and long-term user monitoring. In some cases, that cost is limited to targeted advertising. In others, it extends to financial exposure, identity risk, or persistent surveillance that users never knowingly agreed to.
What has changed is not the existence of data collection, but its scale and subtlety. Modern apps are engineered to make consent frictionless and resistance inconvenient. Opting out often requires more effort than opting in, and declining access is frequently treated as abnormal behavior rather than a valid choice.
Recognizing these patterns is no longer a niche concern for technologists. It is a basic requirement for anyone using a smartphone. Choosing not to install an app, revoking permissions, or walking away from a service that demands too much is not paranoia. It is a rational response to an ecosystem where trust is routinely monetized.