Security researchers have identified a new Android malware strain called DroidLock that can lock victims out of their smartphones and demand a ransom payment to regain access, prompting fresh warnings for mobile users worldwide. DroidLock is a sophisticated threat that combines device-locking tactics with extortion messaging, threatening to erase data or render the device unusable unless a ransom is paid within a strict deadline.
The malware primarily spreads through phishing websites and fake apps designed to look legitimate, tricking users into installing a dropper program that then deploys the malicious payload. Once installed, DroidLock requests extensive permissions including Device Administrator and Accessibility Services, allowing attackers to take full control of the phone’s screen, security settings, and sensitive features.
Unlike typical ransomware that encrypts files, DroidLock instead uses a ransomware-style overlay that blocks the user interface and threatens immediate data loss if a ransom is not paid within a specified timeframe, often 24 hours. The overlay typically impersonates a system message or warning and instructs the victim to contact the attacker by email, listing the device identifier as part of the extortion demand.
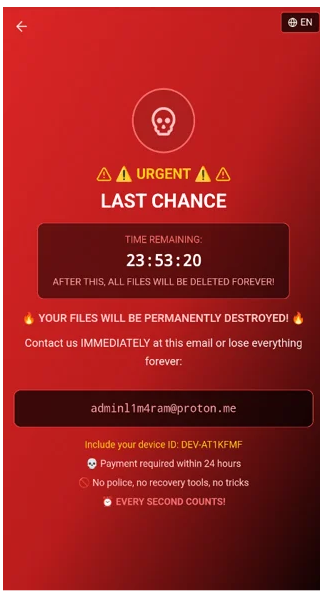
Analysis by mobile security firm Zimperium shows DroidLock can also change the device lock pattern, password, or biometric settings, making it extremely difficult for victims to regain access without intervention. In some cases, the malware can record screen activity or even activate the camera to capture images of the user, potentially for additional leverage or data theft.
The emergence of DroidLock highlights how mobile threats continue to evolve, leveraging social engineering and deep system permissions to bypass security protections. Security experts note that Android remains a major target for malware because of its broad global install base and open app distribution ecosystem.
Users are strongly advised to only install applications from trusted sources, such as the Google Play Store, and to avoid clicking on links from unknown messages or ads. Keeping devices updated with the latest Android security patches and maintaining a reputable mobile security solution can also help detect and block threats before they execute.
In response to attacks like DroidLock and other emerging mobile threats, cybersecurity professionals emphasize the importance of cautious app permissions and regular backups, so users can restore their data if a compromise occurs. While no widespread infections have been confirmed outside initial target regions, the advanced capabilities of DroidLock serve as a stark reminder of the growing risks facing smartphone users today.

 2 min read
2 min read



















