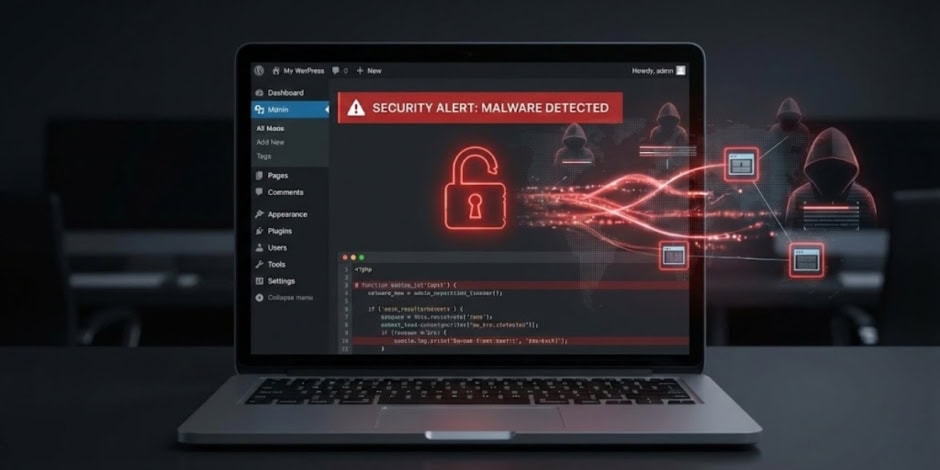
Cybersecurity experts have issued an urgent alert after discovering a new malware campaign exploiting a critical vulnerability in WordPress sites, with more than 40,000 websites believed to be infected or at risk, according to recent analysis by security researchers. The flaw is being actively abused by attackers to compromise sites, inject malicious code, and hijack traffic for unauthorized purposes.
The problem stems from a weakness in an older and widely used WordPress plugin. While the specific plugin has not been named in every report, security advisories indicate that sites running outdated versions of certain themes and extensions remain especially exposed if they have not patched known vulnerabilities.
Once exploited, the malware can do a range of harmful activities:
- Insert spam or phishing content into pages
- Redirect visitors to malicious or scammy sites
- Load cryptojacking scripts that steal CPU cycles to mine cryptocurrency
- Harvest visitor data for further fraudulent use
Because WordPress powers nearly 43% of the entire web, the impact of such a flaw can be far-reaching. Threat actors are actively scanning for vulnerable sites, and many have already deployed automated tools to infect unpatched installations.
Attackers are leveraging automated scanners to identify WordPress sites running the vulnerable plugin or outdated core installations. Once found, malicious payloads are injected into theme files, header scripts, or database entries so that every visitor to the site unknowingly loads harmful content.
In many cases, site owners are unaware their platforms have been compromised until reports of abnormal traffic, SEO penalties, or user complaints begin to surface. Compromised sites can also suffer search engine ranking drops if Google flags them for malware.
Security analysts note that the majority of affected sites share common traits:
- Outdated WordPress core versions
- Unused or obsolete plugins and themes
- Sites without active security monitoring
- Platforms lacking two-factor authentication
Smaller businesses, blogs, and older websites that haven’t regularly updated their infrastructure are disproportionately represented among the vulnerable populations.
If you manage a WordPress site, experts recommend the following immediately:
- Update WordPress Core & Plugins: Ensure the latest stable WordPress version is installed.
- Remove Unused Extensions: Delete obsolete themes and plugins you no longer use.
- Scan for Malware: Use reputable security plugins like Wordfence, Sucuri, or MalCare to perform a deep site scan.
- Check File Integrity: Compare core files against originals to identify injected code.
- Change Credentials: Reset admin and FTP passwords, and enable multi-factor authentication.
Security professionals emphasize that staying proactive is critical: once a site is infected, simply patching the vulnerability may not remove every trace of malware. Full cleanup and verification are often necessary to ensure the site is safe for visitors again.

 3 min read
3 min read