WhatsApp has become the primary propagation channel for an active banking malware campaign after cybersecurity researchers confirmed that the Astaroth trojan is now spreading through a self-replicating worm that abuses compromised user accounts. Official sources said the malware is already circulating at scale, marking a material escalation in how financial cybercrime leverages trusted consumer messaging platforms.
According to confirmed threat intelligence reporting, the campaign uses infected WhatsApp accounts to automatically message contacts with malicious attachments or links, enabling the malware to spread laterally without continuous operator involvement.
“When the victim extracts and opens the archive, they encounter a Visual Basic Script disguised as a benign file,” the cybersecurity company that undertook the threat reporting told media. “Executing this script triggers the download of the next-stage components and marks the beginning of the compromise.”
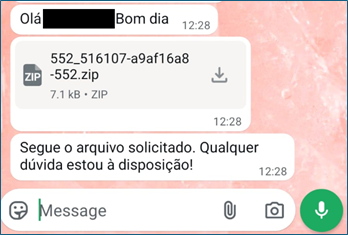
The campaign begins not with a suspicious email or unfamiliar link, but with a WhatsApp message from a real contact whose account has already been compromised. Victims receive what appears to be an ordinary document, invoice, receipt, or image file, often framed in casual language that matches the tone of prior conversations. Because the message originates from someone the recipient knows, the usual warning signs of phishing are largely absent.
Once the attachment is opened on a Windows system, the malware chain activates through a series of intermediate loaders rather than a single executable file. These early stages rely heavily on legitimate Windows tools such as PowerShell and other native scripting engines, allowing the malware to execute without immediately dropping a recognizable malicious file to disk. This design significantly reduces the chance of detection by traditional antivirus software.
The real payload is assembled dynamically in memory. Astaroth uses extensive obfuscation, encrypted strings, and runtime reconstruction to conceal its core components. Before fully activating, the malware performs checks to determine whether it is running inside a virtual machine, sandbox, or system protected by advanced security tools. If defensive software is detected, execution may be delayed or halted entirely, allowing the malware to evade automated analysis.
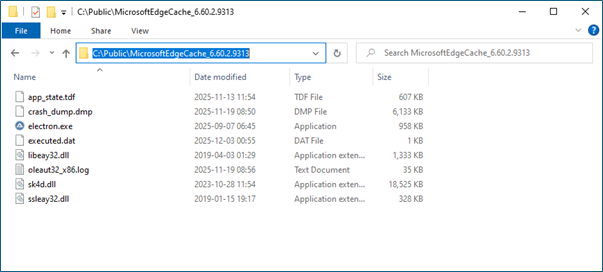
Once the environment is deemed safe, Astaroth establishes persistence using trusted Windows mechanisms. It blends into the system by masquerading as legitimate scheduled tasks or registry entries, ensuring it survives reboots while remaining difficult to spot during routine inspection. From there, the malware activates its banking-focused capabilities.
The operation, which has been active since at least September 24, 2025, downloads ZIP archives with a downloader script selecting one of several PowerShell or Python scripts to harvest WhatsApp user data to continue its spread, and an MSI installer, which installs the trojan.