Security researchers have uncovered a highly advanced Android malware campaign capable of spying on phone calls, intercepting messages, and silently harvesting sensitive user data, underscoring how mobile spyware has evolved from crude scams into full-scale surveillance tools.
This malware is termed as Arsink, a malware designed to aggressively harvest private information once it enters a device. For more technical readers, it is a cloud-native Android Remote Access Trojan (RAT) that aggressively collects private data and gives remote operators intrusive control over infected devices. Researchers have noticed several variants that utilize Google Apps Script to upload larger files and media to Google Drive, or use Firebase Realtime Database along with Firebase Storage and Telegram for command and control (C2) and data exfiltration.
As Zimperium researchers note:
The operation’s significant scale is evidenced by the 1,216 distinct APK hashes identified across the observation period (Figure 1). Notably, 774 of these samples incorporate Google Apps Script or “macro” upload mechanisms, pointing to the extensive use of Google services for media and file exfiltration. The operation leverages 317 distinct Firebase Realtime Database endpoints as C2/data sinks, and our infrastructure enumeration extracted 45,000 unique victim IPs, demonstrating both scale and breadth of exposure.
Unlike common adware or basic banking trojans, this malware operates more like commercial-grade spyware. Analysts say it is designed for long-term persistence and covert monitoring, allowing attackers to track communications, steal credentials, and remotely control infected devices without triggering obvious warnings. Once installed, victims often remain unaware that their phones are compromised.
Researchers have found that malware is primarily spread through social engineering tactics. Instead of relying on the Google Play Store, these malicious apps are often promoted through Telegram channels, Discord posts, third-party websites, and various download links. To trick users into thinking these apps are legitimate, cybercriminals frequently exploit popular platforms like Google, WhatsApp, Instagram, YouTube, Spotify, Facebook, and TikTok. They often label files as “mod” or “premium,” which can mislead users into believing they’re downloading an enhanced version of a familiar app.
As the research report points out, Pakistan was among the most heavily affected.
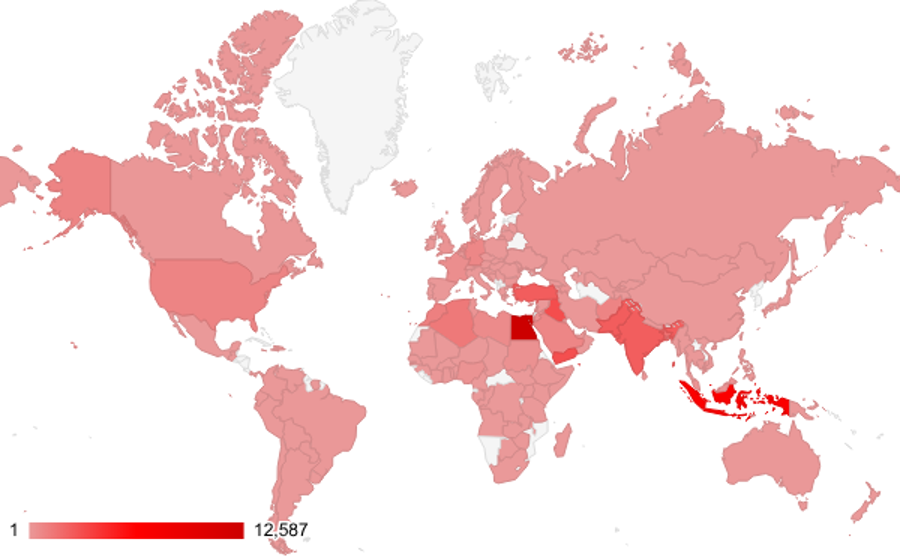
The Arsink operation has a truly global footprint, as it is not confined to any specific geographic area. From the analysis of victim telemetry and publicly accessible C2 dumps, we identified ≈45,000 unique infected IP addresses spanning some 143 countries across the Middle East, Asia, Africa, Europe, and the Americas.
The largest concentrations were observed in Egypt (≈13,000 devices), Indonesia (≈7,000), Iraq (≈3,000), Yemen (≈3,000) and Türkiye (≈2,000). Notable clusters also appear in Pakistan (≈2,500), India (≈2,500), Bangladesh (≈1,600), and North African countries such as Algeria and Morocco (each ≈1,000), regions where third-party APK distribution and Telegram sharing are common.
Once activated, the malware aggressively abuses Android’s permission system. After gaining elevated access, it can:
- Intercept and exfiltrate call logs and SMS messages
- Record phone calls and ambient audio through the microphone
- Capture screenshots and monitor screen activity
- Steal contacts, stored files, and saved credentials
- Bypass two-factor authentication by reading one-time passcodes
- Execute remote commands via encrypted command-and-control servers
Google has confirmed that certain versions of Arsink are not available on the Play Store. They also noted that Android devices with Google Play Protect turned on will automatically receive protection warnings.
On top of that, the company has teamed up with researchers to take down parts of the malware’s infrastructure, including some harmful cloud endpoints.

 3 min read
3 min read



















