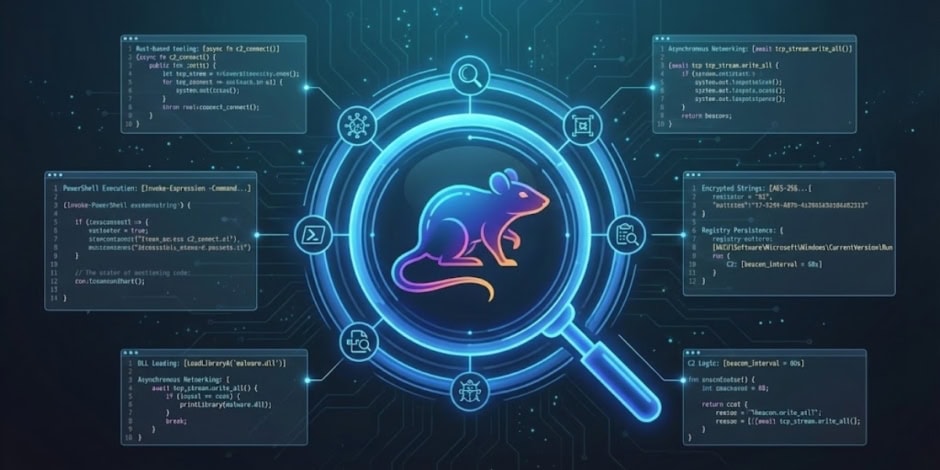
Security researchers have confirmed that the Iran-linked advanced persistent threat group MuddyWater APT has launched a spear-phishing campaign deploying a Rust-based remote access Trojan (RAT) named RustyWater against organizations across multiple Middle Eastern sectors, according to cybersecurity intelligence reports.
The campaign, identified by threat analysts at CloudSEK, uses crafted spear-phishing emails that impersonate credible sources and contain malicious Word documents. Victims are enticed into enabling macros inside the document, which then triggers a chain of execution that delivers the RustyWater implant onto the victim’s system.

RustyWater kicks off its operation by setting up mechanisms to prevent debugging and tampering. It employs a Vectored Exception Handler (VEH) to intercept any debugging attempts and methodically collects information from the victim’s machine, such as the username, computer name, and domain membership. All the strings within the malware are encrypted using position-independent XOR encryption. Some of the decrypted strings discovered in the binary included:
- “C:\\ProgramData”
- “SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run”
- “Mozilla/5.0 (Windows NT 10.0; Win64; x64)”
- “reqwest/0.12.23” // Rust HTTP library
- “Content-Type: application/json”
Once executed, RustyWater establishes persistence by modifying the Windows Registry, maintains low-noise communications with a command-and-control infrastructure, and supports asynchronous control operations that enable remote attackers to execute commands, transfer files, and gather system information.
Analysts note that this represents a significant evolution in MuddyWater’s tooling. Historically, the group relied on scripted loaders such as PowerShell and VBScript for post-compromise activities. By deploying a Rust-based implant, investigators say the threat actor is embracing a more structured, modular approach that enhances stealth and resilience against legacy defenses.
MuddyWater, also tracked under aliases such as Mango Sandstorm, Static Kitten, TA450, and Earth Vetala, has been active since at least 2017 and is widely assessed by cybersecurity entities as being aligned with the Iranian Ministry of Intelligence and Security (MOIS). Its historic targeting spans government, critical infrastructure, telecommunications, and private enterprise across the Middle East, Asia, and beyond.
The RustyWater implant’s capabilities include scanning for installed security software to evade detection, intelligent persistence mechanisms, and flexible command execution. Because the malware communicates over common HTTP/HTTPS protocols with obfuscated payloads, traditional signature-based defenses may struggle to identify or block it without more advanced behavioral analysis.
CloudSEK’s report highlights the sophistication of the spear-phishing lures used in this campaign, noting that the malicious emails and spoofed document icons are designed to appear legitimate and increase the likelihood of user interaction. The targeted sectors include diplomatic, maritime, financial, and telecom organizations, reflecting the group’s continued focus on cyber espionage and information gathering.
Although RustyWater has been observed mainly in Middle Eastern contexts, its modular architecture and evolving tradecraft underline the ongoing threat posed by state-sponsored APT groups to global digital infrastructure.