The US National Security Agency (NSA) had been using a way to hide spying software deep within hard drives made by top manufacturers such as Western Digital, Seagate, Toshiba, IBM, Micron Technology Inc and Samsung Electronics Co Ltd. Western Digital, Seagate and Micron said they had no knowledge of these spying programs. Toshiba and Samsung declined to comment. IBM did not respond to requests for comment. The agency eavesdropped on both personal and government computers in many Asian countries including Pakistan for almost two decades.
Kaspersky Lab, a Moscow-based security software maker has exposed a cluster of spying programs and a series of Western cyber espionage operations. The lab found that personal computers in more than 30 countries have been infected with one or more of the spying programs with the most infections seen in Iran, Russia, Pakistan, Afghanistan, China, Mali, Syria, Yemen and Algeria. The targets within countries included government and military institutions, telecommunication companies, banks, energy companies, nuclear researchers, media, and Islamic activists. The chart below shows a detailed view of the affected areas along with the target institutions within each country.
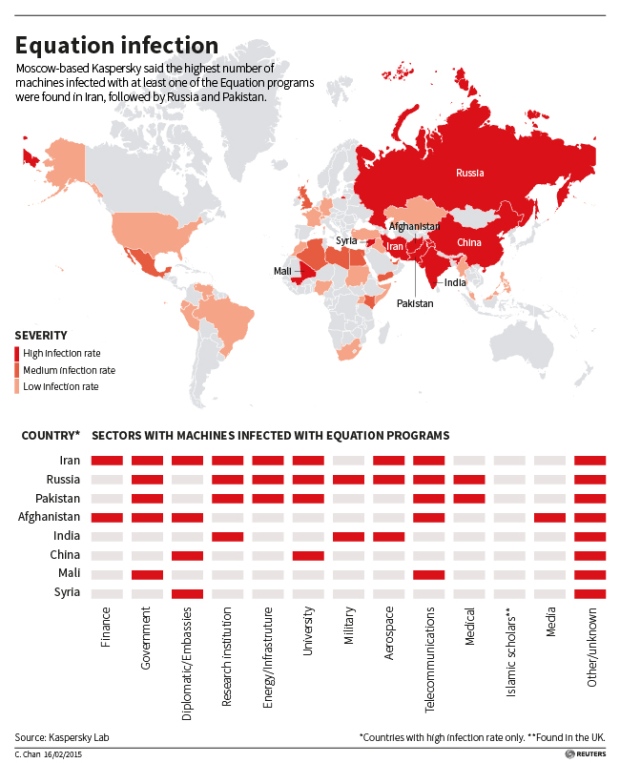
Kaspersky Lab has been closely monitoring more than 60 advanced security threats for several years which were responsible for cyber-attacks worldwide. Recently, they confirmed the existence of “The Equation Group” responsible for spying through hard drives for the past two decades. The Equation Group used tools that were both complicated and expensive to develop. They infected their victims, retrieved data and hid activity in an extremely professional way, and utilized classic spying techniques to deliver malicious payloads to the victims.
The spies figured out how to insert malicious software in the obscure code called firmware that launches every time a computer is turned on. Kaspersky found that they were selective about the target computers and only established full remote control over high-valued foreign computers.
The Lab did not publicly name the country behind the spying campaign but it did mention Stuxnet, the NSA-led cyber weapon which was used to attack Iran’s uranium enrichment facility. Additionally, a former NSA employee told Reuters that Kaspersky’s analysis were indeed correct while another employee confirmed that NSA had developed the technique of concealing spyware in hard drives.
Find out the details on the Malware here.





 Samsung Electronics unveils an array of smart appliances
Samsung Electronics unveils an array of smart appliances