The online community was sent into a shock a few days ago when it was revealed that nearly all modern CPUs are vulnerable to two extremely dangerous exploits — Spectre and Meltdown. Since then, a number of different software manufacturers have taken precautionary measure to reduce the impact of these vulnerabilities through software patches. However, considering that the vulnerability originates at a hardware level and one of them is rooted in the fundamental working of a modern CPU, it is very difficult to make sure that these issues are fixed immediately.
I am getting a little ahead of myself, aren’t I? For those who are still confused about what these vulnerabilities mean and how do they affect you, let me first layout the whole issue in terms that most of us can understand.
How do CPUs normally work?
If you have some rudimentary knowledge of a computer processor, you must know that CPUs work by executing instructions. In simple terms, it works like an obedient worker, it asks for your instruction, executes what you ordered it to do, and when it is done executing that instruction, it asks you for the next instruction. That’s what a normal computer program is; just a set of instructions which are executed one after the other.
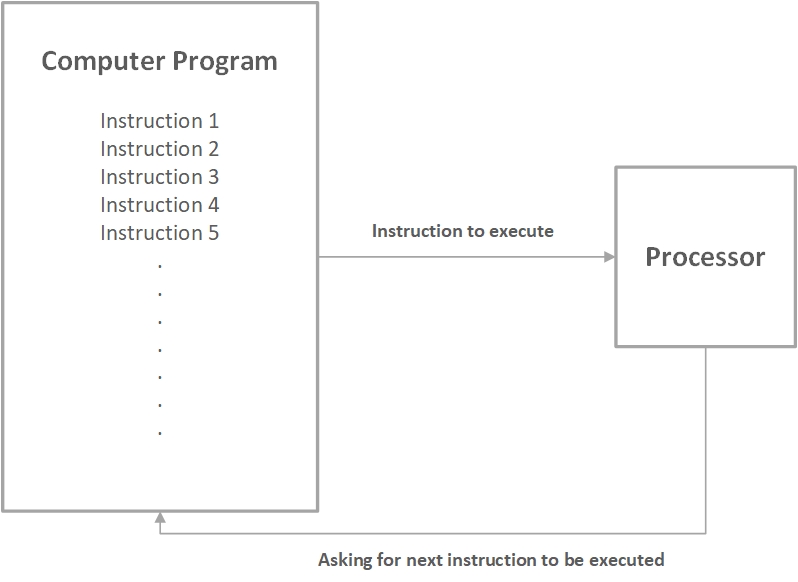
Normally, sometimes a program might jump backward and forwards in that set of instructions. This is done based on some conditions. If a condition is met, a certain portion of instructions is slated to execute, while failure to meet that condition would result in a different set of instructions to be fed to the CPU. This helps in building logic for more complex computer programs.
Modern computers and multiple programs
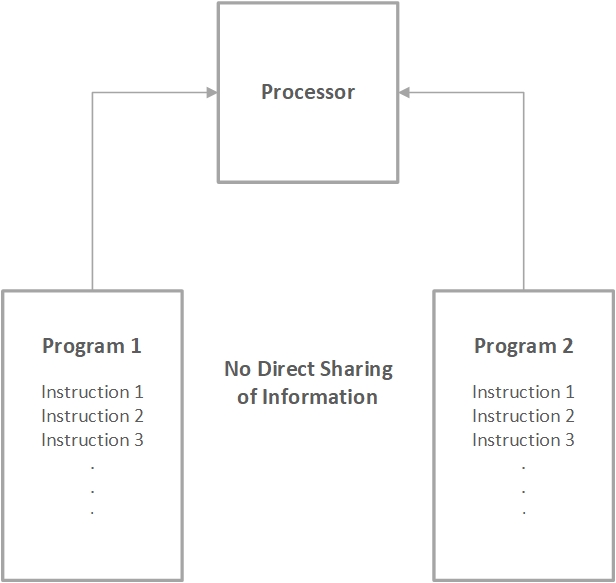
With modern computers, a number of different programs can be run simultaneously (who doesn’t switch between Messenger and WhatsApp continually on their phone these days?). Again, to make things simple, we can assume that these programs run separately on that nice big RAM that you have on your computer. Modern CPUs deploy user space memory isolation barrier, which means that one program cannot access the memory of another program willy-nilly. So let’s suppose that a hacker does gain access to your phone and installs some rogue application on it, it won’t be able to access your WhatsApp messages or Bank account information because it is the property of a different program.
Okay…? So what about those vulnerabilities?
Hang on, I’m getting there. Let’s revisit what we discussed above. So a program works on instructions, which might jump around based on certain conditions, and the memory space of each program is isolated and inaccessible due to security reasons. Talking about those conditions, sometimes checking a condition match takes a very long time (if the condition involves access to a memory, it might be hundreds of CPU cycles), and the CPU has to wait for the condition matching to end and then execute the next instruction. To prevent this waste of time, modern processors use a “speculative approach” towards conditions (that’s where the name Spectre comes from too). So instead of just waiting for the condition to actually match, it predicts whether the condition is met or not. By using the result of that prediction, it continues executing on the assumption that its prediction is right. If, after the condition has been matched successfully, its prediction was right, it just keeps on doing what it is currently doing happily and everything is peachy. However, if the prediction was wrong, it must roll back to the point where it went wrong and start all over again.
This approach is used in nearly every modern processor. Whether it is being used in a laptop, a smartphone, a smartwatch or even a TV (TVs probably won’t have a lot of sensitive information which can get hacked, but still), it is running some form this speculation logic. Spectre, the vulnerability recently discovered, uses this speculation logic and forces a program to run such instructions which would normally not run if the program was executed correctly (the CPU is just predicting the result of the conditions, not actually checking if they work), and run a side channel (this can be used to transmit information to another application) which gives access to that program’s information to that other malicious, naughty little application. This information could be your precious credit card numbers stored in a secure wallet application, or maybe your private messages that you don’t want anyone else to read. It. Can. Be. Anything!
Note: This explanation is simplified a bit and discussion of covert channels and cache management is kept to minimum
Holy… And what about Meltdown?
While Spectre can be used to access data of different applications using this speculation trickery, Meltdown is more dangerous and, thankfully, easier to fix. Remember the userspace memory isolation barrier that modern CPUs maintain? Meltdown basically tears that down (thus the name, Meltdown). Without going into too much technical detail, it does this by getting access to the kernel. The kernel is kind of like the administrator part of an OS. The kernel memory space holds a lot of sensitive information including some personal data and passwords. A Meltdown attack forces the kernel to be loaded into the memory (usually a faster cache memory used to reduce access times) by generating an exception (an error which forces the operating system to intervene). By using a side channel similar to Spectre attack, that malicious application can then access the sensitive information stored in the kernel, and through access to the kernel, it can gain access to all the other applications on the device.
A lot more information about both these exploits and complete research papers are available at the homepage of meltdown attack maintained by the Graz University of Technology.
Patching up these vulnerabilities
Although Meltdown is the scarier of two vulnerabilities, it only affects Intel processors (so like 95 percent of all laptops and computers? phew…) and it is easier to mitigate against. Many manufacturers have already started taking measures against both vulnerabilities by releasing software updates and hotfixes.
Spectre is a different story though. It is deeply rooted in how the CPU works and is more difficult to take measures against. Unless Intel and other chip manufacturers release updated microcode for their CPUs, which drastically changes the working of their chips, Spectre is going to remain a big issue for the foreseeable future. However, exploiting a Spectre vulnerability is not an easy task, and thus it might not be possible for hackers to cause damage at a very large scale, very quickly.
Is my computer going to slow down now?
In simple terms, yes. After using the patches that Microsoft and other manufacturers are releasing, there might be some degradation in the CPU’s performance. It was speculated in the beginning that the performance impact would be more than 30 percent, but as more information is released by Google and other manufacturers about the fixes being released, it is being claimed that the performance impact would be minimum
Am I safe now?
You are most probably as safe as you can be if you have the latest software and don’t intend to install every application you find on a shady part of the internet. However, the impact of Spectre is too large to be eliminated immediately. It affects nearly all processors and is harmful to an application to application basis. Heck, as pointed out by Jake Williams, information security specialist, there’s even a proof of concept of a JavaScript implementation of Spectre.
Spectre has a ready made JavaScript implementation. 2018 is going to be awesome(ly horrifying) pic.twitter.com/VkIPrm8ko8
— Jake Williams (@MalwareJake) January 4, 2018
Most antiviruses are currently ineffective against malicious applications making use of Spectre and Meltdown (to be honest, there probably aren’t any malicious programs in the wild which make use of these vulnerabilities). However, using the community-based detection that most AVs these days use, it is advisable to keep one running to take advantage of what little protection they might provide against these vulnerabilities.
Image Source: The Hacker News




 8 productivity tips that will change the way you look at work
8 productivity tips that will change the way you look at work