The Cisco 2017 Annual Cybersecurity Report presents research on the most commonly observed malware.
Cisco is a global IT leader that provides cyber intelligence and advanced threat protection portfolio to the organisations. It works on reshaping the internet for better and addressing customers’ challenges.
Malware, short for malicious software, is a program that can infiltrate and damage your PC, access sensitive information or disrupt your mobile operations. The general terms for such threats are virus, spyware, adware, ransomware, worms, trojans, toolkit and so on.
As the world is moving towards digitization, the online workspace is increasing which, in turn, is expanding the surface of attack. The strategies of attackers include:
● Taking advantage of lapses in patching and updating
● Luring users into socially engineered traps
● Injecting malware into supposedly legitimate online content such as advertising
According to the Security professionals, Mobile devices, Public cloud, Cloud infrastructure and User behavior are the biggest risk of exposure to a cyber attack.
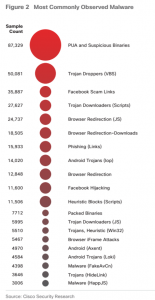
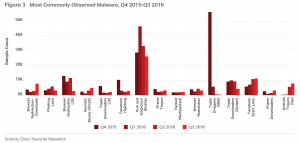
Most Commonly Observed Malware
1. Reconnaissance is an initial step for launching a cyberattack. In this phase, attackers look for vulnerable spots in internet infrastructure or network weaknesses that will allow them to gain access to users’ computers and, ultimately, to infiltrate organizations.
2. Suspicious Windows binaries and potentially unwanted applications (PUAs). Suspicious Windows binaries deliver threats such as spyware and adware. Malicious browser extensions are an example of PUAs.
3. Facebook scams include fake offers and media content along with survey scams. Facebook has nearly 1.8 billion monthly active users worldwide which makes it a logical territory for cyber criminals.
4. Trojan Downloader made it to 4th on the list. It is installed through opening links in spam emails or an image download which affects victim’s computer.
5. Browser redirection malware was the 5th most commonly observed malware of 2016. Browser infections can expose users to malicious advertising (malvertising), which attackers use to set up ransomware and other malware campaigns.
6. Browser Redirection-Downloads not only redirect the browser but also download the malicious malware to the computers.
7. Phishing Links are a way of deceiving users by redirecting them to a spoofed website that looks legitimate.
8. Android Trojans have been moving steadily up the short tail list over the past 2 years. Loki malware is the example of that. It encrypts your files and then demands ransom in order to give you the key to get them back.
9. Facebook Hijacking is another way of hacking. The malware posing as Chrome extension or Firefox add-on threatens your security.
10. Heuristic Blocks This Trojan can enter your PC in many ways and harms your data, corrupts your files and even delete them. It also reduces CPU performance.
Users should find the vulnerabilities and patch them with some antivirus. This way attackers will find it extremely difficult to gain access to valuable information. Organisations must focus their resources on reducing the attackers’ operational space. Automation can help organizations understand the threats. They should use security safeguards —prevention, detection, and mitigation—to minimize risk.






 Xiaomi is finally launching in Pakistan on Feb 20
Xiaomi is finally launching in Pakistan on Feb 20
4 Replies to “These are the top 10 malware that can breach your security”
Comments are closed.