These days simply having a complicated password with a few questions about your favorite pet or food isn’t just enough hence this is where multi-factor authentication comes into place to prevent all sorts of data breaches. This works by adding more security layers to the application or website you or others try to access to ensure that only the owner of the account or platform has access.
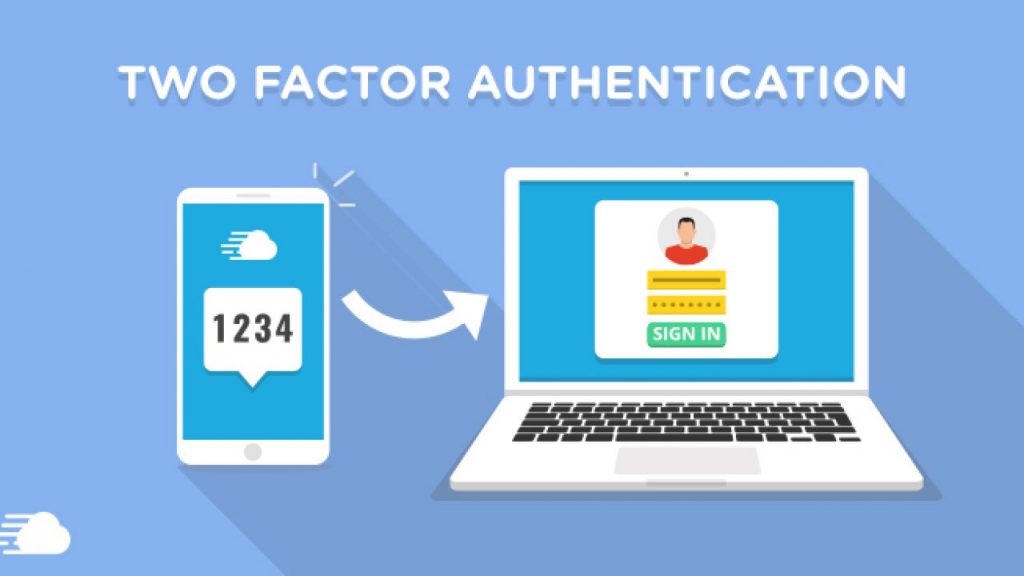
The most common form of multi-factor authentication is two-factor authentication (SFA) which works by adding an additional layer of security to whatever platform you access. 2FA requires additional login credentials such as a passcode, Touch ID, or something that only the owner of the account can access.
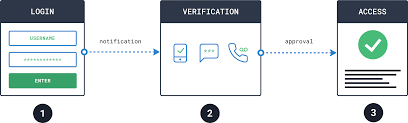
This sort of method is necessary because it prevents hackers from stealing passwords and emails through malicious emails and websites.
Read More: Billions Of Passwords Leaked In The Largest Data Breach
Types of two-factor authentication
Two-factor authentication varies from platform to platform especially in terms of applications that store sensitive data such as bank details, passwords, phone numbers, etc. Here are some of the types of 2FA’s:
1. Text message 2FA
If you ever have used Gmail (which is mostly something everyone does) or platforms such as Discord you may have noticed they ask for a code to enter after you have placed in your email and password to log in.
How this works is that if you have provided your phone number to the service you are using you will receive a text message from the service providers which contains a code. Once you have entered the code, you will receive access to the platform you are trying to get into.
The benefit of this is that unless your phone number isn’t public then it is very unlikely that hackers will be able to hack your account. This mostly works with banking applications as well that require you to enter the code sent to you before you can get started with online banking.
2. Authentication applications
These are basically applications that are available on both iOS and Android. If you’re a Discord user or use GitHub then such platforms use apps such as ‘Authenticator’ to generate the code rather than relying on your smartphone.
How this works is that the authentication application installed on your phone simply does nothing but six-digit codes for the services you use. These codes have a time limit though, so if you were to use the code you see on your app after 1 minute then that code will not be valid and the app will simply generate another code and the process continues on.
This is like the alternative way if your phone number is public on your respective social media profiles.
3. Biometric authentication
Just by the term ‘biometric’ you most probably know how this works. For those who don’t know, this method of authentication is solely dependent upon factors such as fingerprints or retina scans.
Though this seems high, secure this form of data being stored by services seems rather frightening as you just can’t simply change your fingerprints or how your eyes and their respective retinas.
Is it really secure?
Now the main question here is that, is two-factor authentication really a secure option? Currently, it’s more of a 50-50, it’s both a yes and a no. Because although text messages and authentication applications are super secure, what are the chances a user loses his or her phone? Then that means there is a loophole in this form of security as well.
Then comes biometric authentication, though it also seems super secure as of now criminals can replicate fingerprints by placing the scanned prints on butter paper and printing out the hologram. Similarly, numerous crimes in Karachi were committed in terms of fraud due to this very same method.
This can be said for retina scans as there are even ways to duplicate retinas given the data and tools to duplicate them are efficient.
How do we keep our accounts secure then?
With so many loopholes, one just wonders that if there really is a way to be entirely secure without hackers trying some method to bypass the security. Well although new forms are being worked on by numerous companies, here are some practices you can implement to ensure you are secure even through the 2FA method:
- Use another number for text message 2FA instead of your personal number.
- Do not use email to reset your accounts.
- Use multiple authentication methods instead of just one.
Let us know in the comments below what methods of security do you prefer for your accounts.




 Successful 5G Trial Held In Peshawar Despite Of Limitations
Successful 5G Trial Held In Peshawar Despite Of Limitations