The Heart bleed bug has been a hot topic for the past few days, and for a good reason too. It is a serious vulnerability in online communication security that can leak your credentials like usernames and passwords, and other private particulars like bank account details, to the hackers. The flaw has been around for quite some time now, and unfortunately there’s no telling how much of the data on the internet has been stolen or compromised as of yet.
What is Heartbleed?
There’s a lot of communication and data transfer taking place all over the span of the Internet each day. In order to protect this data from eavesdroppers, the providers of web, IM, email and related services implement different security protocols. One of these protocols is TLS/SSL (Transport Layer Security/Secure Sockets Layer), which uses the concept of public key cryptography. OpenSSL is an open-source implementation of this security protocol and this is where the problem lies: OpenSSL had a serious flaw in the latest version of its library, the TLS Heartbeat extension (hence the name Heartbleed) which could essentially put every server that uses this security technique at huge risk.
This Heartbleed bug is not new—it was introduced in the software library of OpenSSL back when it was being coded (which was December 2011), and it’s been out in the wild ever since OpenSSL’s affected version (v1.0.1) was released in March 2012.
Who Caught it, and How Widespread is the Problem?
The Heartbleed bug was discovered independently by the security team at Codenomicon and Google Security’s Neel Mehta. It was immediately reported to OpenSSL by the latter and their team started working on a fix.
The Heartbleed bug—to summarize the danger it poses—puts every piece of communication between a user and a server that uses OpenSSL, at the risk of being exposed to a third party. Classified as a “buffer over-read” bug, the flaw can let a hacker act as a server to request data directly from a user, and vice versa. Any hacker can grab a 64kB chunk of data from the server memory with every “heartbeat” (a period of connectivity between server and client). 64kB may not seem much, but there is not limit on how many times this process can be repeated to request data from servers. Once a hacker grabs a hold of meaningful chunks of data, they can access the private key of that server which essentially puts all of the data present on the server at the mercy of hacker: this data could include usernames and their account passwords, bank and credit card details, confidential pieces of information, and so on.
OpenSSL is only one implementation of the TLS/SSL security protocol, and only the systems using v1.0.1 (a through f) of OpenSSL are vulnerable to attacks, but the bad news is that 2 out of every 3 servers around the world use this encryption technique. What makes the matters even worse is that it took 2 years to discover the flaw and it is not possible to ascertain the amount of damage it has caused so far because no abnormal activity is recorded or logged when this vulnerability is used to request data from the systems. It is possible that zero to very little amount of data was compromised during this period but again, there’s no way to confirm that.
Generally, any server that is running OpenSSL on Apache or Nginx is at risk. According to NetCraft, about 17.5% of SSL sites have Heartbeat extension enabled, which puts the number of at-risk websites at around half a million. Servers from firms like Yahoo, Pocket, Flickr, GitHub, Imgur, StackOverflow and numerous others were reported to be vulnerable. Here’s a pie-chart that shows the servers-distribution according to a recently-conducted survey:
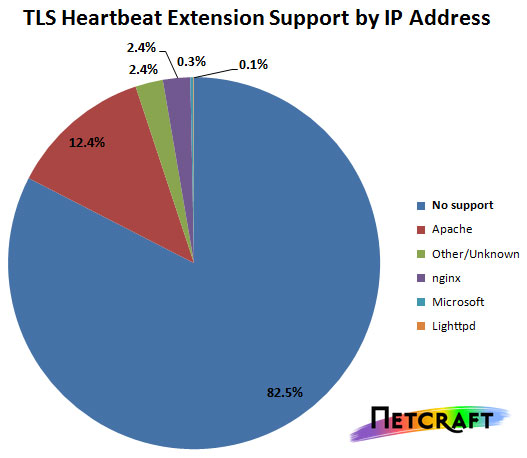
Is There Something I Can Do to Stay Safe?
As soon as the vulnerability was reported, OpenSSL team started working on a fix—v1.0.1g—and it was immediately released for the servers using OpenSSL. Now it is up to the service providers which were using the vulnerable version of the library to update their OpenSSL protocol to the latest one.
As far as Pakistan’s Internet market is concerned, the specific details are quite obscure because of the lack of statistics-based reports, but still you can take some precautionary measures to keep your data safe. If you use web-hosting services from local companies, you should ask your service provider if they use OpenSSL and whether or not they have patched their servers against the vulnerability. If you use dedicated servers, then it is highly recommended that you demand a renewed SSL certificate for your domain as well, since the keys based on older certificates are highly likely to have been leaked.
Hosting service providers like GoDaddy, Akamai Technologies and AWS have fixed the SSL issues with their servers. GoDaddy is also offering to re-key the SSL certificates free of cost; be sure to take advantage of that, if necessary. A detailed guide on re-keying the SSL certificate has also been provided by GoDaddy here.
If you run service(s) that use OpenSSL certificate, you may want to test if your server has been exposed to the vulnerability. Several test tools have been launched since the bug was reported; a few of them are:
- LastPass’s Heartbleed Test: https://lastpass.com/heartbleed/
- Filippo’s Server Test: http://filippo.io/Heartbleed/
- Heartbleed Test from Rehmann.co: http://rehmann.co/projects/heartbeat/
- Qualys SSL Labs: https://www.ssllabs.com/ssltest/analyze.html
If the servers are affected, you should update the OpenSSL protocol with the latest fixed version (v1.0.1g). If this is not an immediately-possible option then consider recompiling OpenSSL code after handshake removal by the compile-time option -DOPENSSL_NO_HEARTBEATS.
On the other hand, if you are a user then changing the password will only be beneficial if a fixed version of OpenSSL has been implemented by your service provider. Even changing a password won’t do much otherwise, since the servers will still be assailable against the attacks. If your service provider, however, updates their SSL protocol to a secure one, changing the password is the most viable option in that scenario.
The big names like Google and Yahoo were among the first to act, and they report to have fixed any flaw and encourage the users to reset their passwords for services like Google account, Yahoo! Mail, Flickr, Tumblr etc. All the significant service providers who have since reported to patch their services and recommend an immediate password change from their users are:
- Akamai Technologies (content delivery network; used by a number of service providers)
- Amazon Web Services (not required for Amazon.com; recommended for AWS)
- Ars Technica (IT news and information)
- Dropbox
- Facebook (not explicitly affected; password change recommended)
- GitHub (repository and revision control manager)
- Google (Search, Wallet, Play, Gmail etc.)
- Intuit
- LastPass (password manager; uses several layers of security but a password change is recommended)
- Mojang (game developer; accounts for Minecraft etc.)
- OKCupid
- PeerJ
- SoundCloud (audio sharing service)
- SparkFun (electronics retailer)
- Stripe (online transactions and payment service provider)
- Yahoo (for Yahoo! Mail, Tumblr, Flickr and other services)
- Wikimedia
- Wunderlist
If you use any of the services listed above, consider changing your password at the earliest. You’ll have to wait for rest of the companies to patch their code before you change the password for those. Services which do not use OpenSSL or the offending version of OpenSSL in particular, and hence remain safe, include Microsoft, Outlook/Hotmail, LinkedIn, AOL, Target, eBay and most of the banking networks.
-Images and source credits: CNN, NetCraft, TheVerge, Mashable




 Govt. Refuses to Delay 3G/4G Licenses’ Auction Against the Advice of Senate Committee
Govt. Refuses to Delay 3G/4G Licenses’ Auction Against the Advice of Senate Committee
Comments are closed.