The growth of social media and our presence online gives us a lot of opportunities for connecting, socializing, collaborating etc. However, due to the nature of online social media networks, harm can be done to someone if their personal information available is accessible to users with malicious intent. In addition to being careful about what sort of information we share online, we should also take precautions against the worst case such as losing control of an account to an attacker.
While there are rare cases where hackers manipulate vulnerabilities in a website’s security system, most of the times successful attacks are due to the lack of knowledge or carelessness of users regarding security.
Facebook is by far one of the most popular social media networks and has been the subject of all levels of attacks. Following are some of the methods that can be used by potential attackers to gain access into Facebook accounts and how you can avoid being a successful target by taking simple precautions.
1) Password Reset
This method uses Facebook’s facility to recover forgotten passwords in order to gain access to a victim’s account. For this to work, the attacker has to know the e-mail address that the victim uses for his/her Facebook account so that the “forgot your password” feature works. Then, the attacker either has to answer the secret question or enter codes that Facebook generates and sends to a number of trusted friends. Submitting all these codes to Facebook gives the user the access to his/her account.
Precautions
Ideally, the e-mail address used for Facebook account should be different from the one used for other accounts and it shouldn’t be visible on the profile. Also, the secret answer can usually be guessed or tricked out of an unsuspecting victim (social engineering). To avoid such a situation, the secret answer should always be something only you would know. Maybe it isn’t even a direct answer to the secret question. This way guessing it based on information about you extracted from you, your friends or other online profiles wouldn’t be possible.
Some users are also in the habit of accepting friend requests from random people they don’t know. Attackers can use this by befriending such a person and then sending out the one-time codes to their own accounts. So one should only accept friend requests from people they know and have the list of trusted friends should only have those whom can be truly trusted.
2) Stolen Cookies
Cookies allow a website to store information on a user’s system and later retrieve it. These cookies contain important information used to track a session. This information helps websites identify users and allow a customized experience, among other things. But this information also allows hackers to access the victim’s account. These cookies can usually be stolen via different software tools that “sniff” the communication through an open Wi-Fi connection.
If the user is still logged in, the attacker can use these cookies to access the victim’s account by cloning the cookies and tricking Facebook into thinking that the attacker’s browser is already authenticated.
Precautions
First and foremost, Facebook (or any other website to which there is sensitive communication) should only be browsed securely (with HTTPS rather than HTTP protocol. This is visible in the URL bar of the browser).
Secondly, one should log off every time they are done using such a website and access them via trustworthy or secure Wi-Fi networks only.
3) Phishing
Phishing means getting sensitive information (passwords) by tricking the user into thinking they are entering the information to a trustworthy site. It is usually a website that has the same interface as the one a user wants to access. The victim is given the link in an official looking e-mail or a chat, online forum etc. As everything looks fine, the user enters the information into the fake site and it is received by the attackers.
Precautions
Links received in an e-mail should be accessed with extreme care. Unless they were requested by the user (for forgotten password or change of information), the link is most probably false.
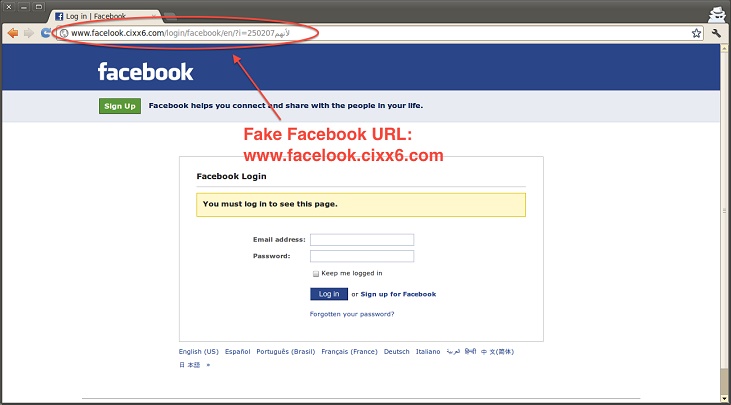
Phishing is also easily identifiable by looking at the site’s address (URL) in the browser’s URL bar. The address would be similar to, but different than the real address of the site you want to visit and it cannot be accessed securely (via HTTPS).
4) Accessing browser’s saved Passwords
When users choose to save their passwords for automatic login, browsers save the log-in IDs and passwords in files at specific locations on the user’s hard drive, depending on the browser and OS. There are software tools that can access these saved passwords and decrypt them. Originally developed for investigations in cyber-crimes, they can be easily used for committing cyber-crimes.
Precautions
While browsers are continuously updated and such threats are tackled, it is still an ever-present vulnerability. The best way to avoid this is not to use the “Remember Me” option during log-ins or save passwords. A few seconds of inconvenience can save us from a security disaster.
5) Keyloggers
Keyloggers are programs or hardware attachments that record keystrokes of a user. The recorded keystrokes are usually transmitted to the attacker via e-mail. To use it, an attacker first needs to gain physical access to the target systems to install the keylogger or trick the user into installing it himself via a trojan (for a software keylogger). For some simpler keyloggers, the attacker has to come back to the system to retrieve the data and the keylogger.
Precautions
It is relatively difficult to install keyloggers since physical access is required and hardware keyloggers can be identified visually. Nevertheless, firewalls should be used to ensure that no program is secretly communicating through the internet. Furthermore, frequently changing passwords reduces the time span within which a stolen password might be useful to an attacker.






 Pakistani telecom companies overcharging subscribers & avoiding taxes
Pakistani telecom companies overcharging subscribers & avoiding taxes